While dabbing in the technical realm of cyber security, I looked for open-source honeypot platforms to experiment with. After discovering a long list of possible options, I decided to deploy an instance of Deutsche Telekom Security’s T-Pot.
Utilizing Docker for containerization, T-Pot runs the following honeypots simultaneously on a single host.
- adbhoney,
- ciscoasa,
- citrixhoneypot,
- conpot,
- cowrie,
- ddospot,
- dicompot,
- dionaea,
- elasticpot,
- endlessh,
- glutton,
- heralding,
- hellpot,
- honeypots,
- honeytrap,
- ipphoney,
- log4pot,
- mailoney,
- medpot,
- redishoneypot,
- sentrypeer,
- snare,
- tanner
To make it easy to search through and visualize the data generated by various malicious bots in the IPv4 address space, T-Pot features ElasticVue, as well as the Elastic Stack, consisting of Elasticsearch, Logstash, and Kibana. A real time attack map showing attacks on a global map in real time, is also included, which unfortunately broke before I was able to take a screenshot of it.
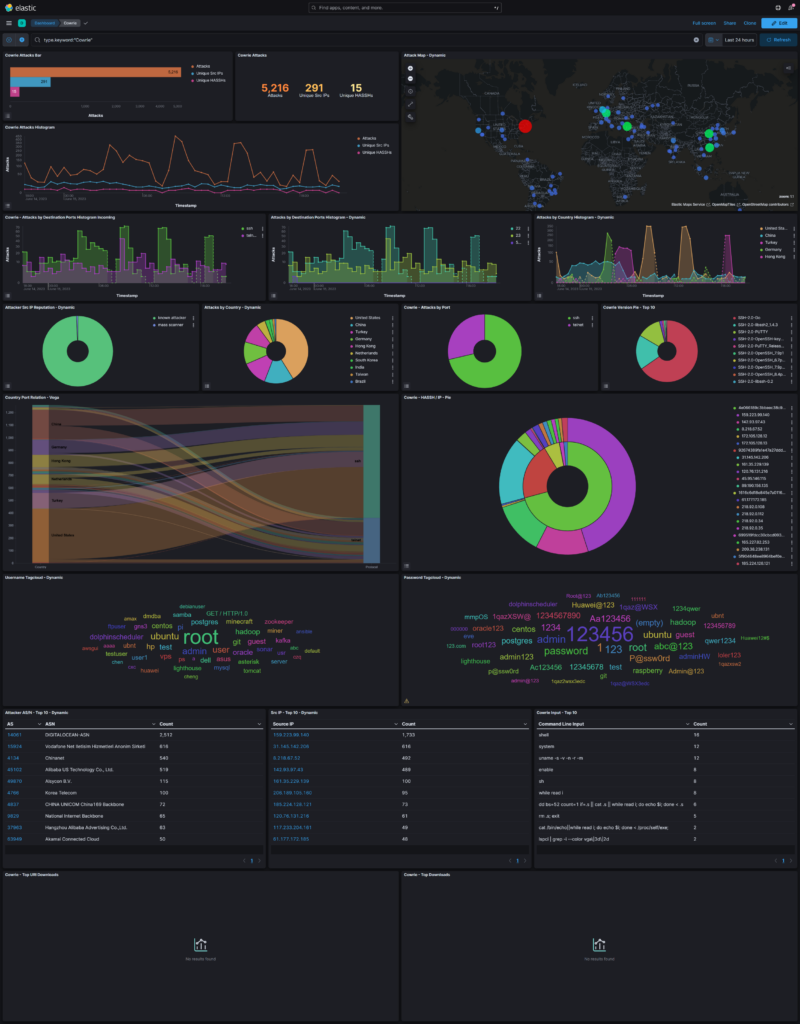
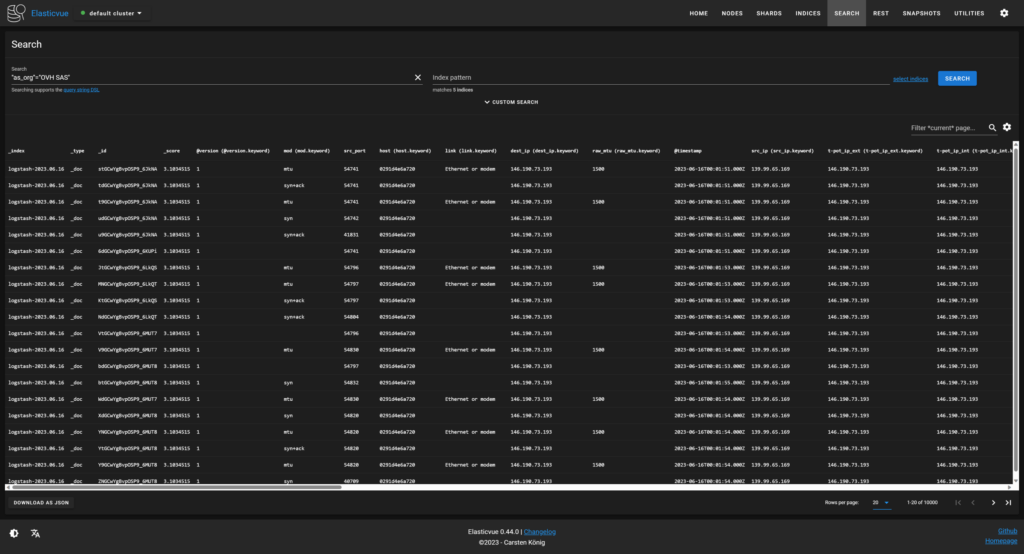
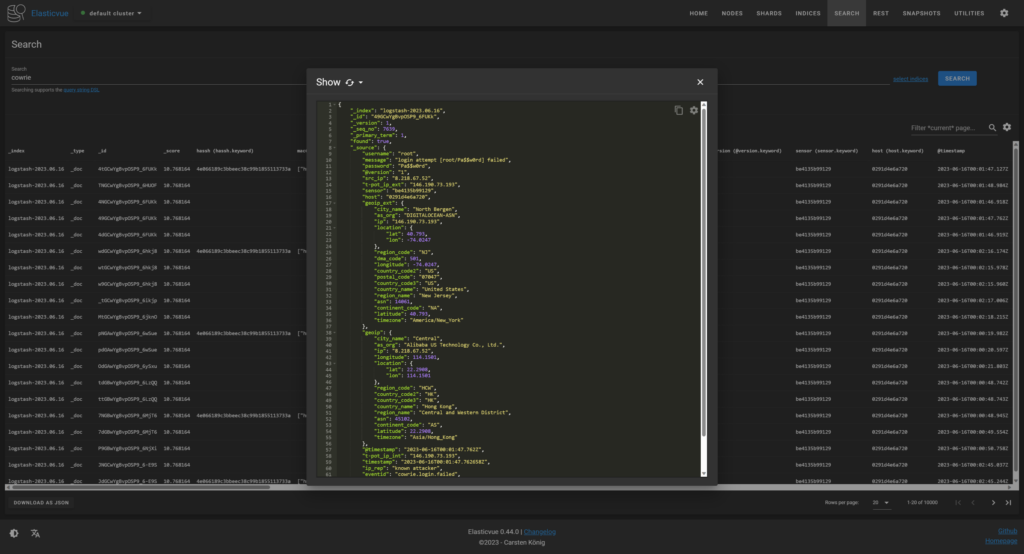
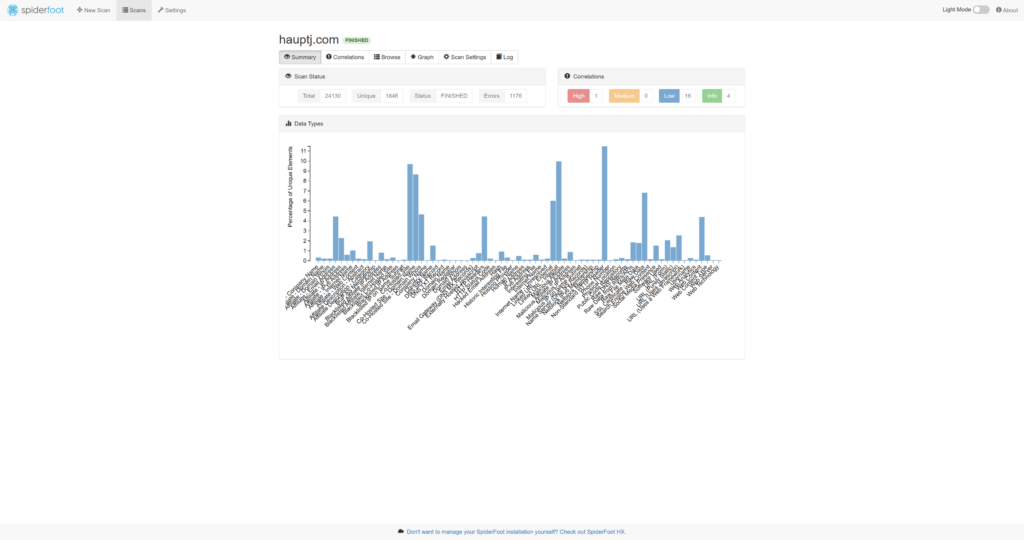
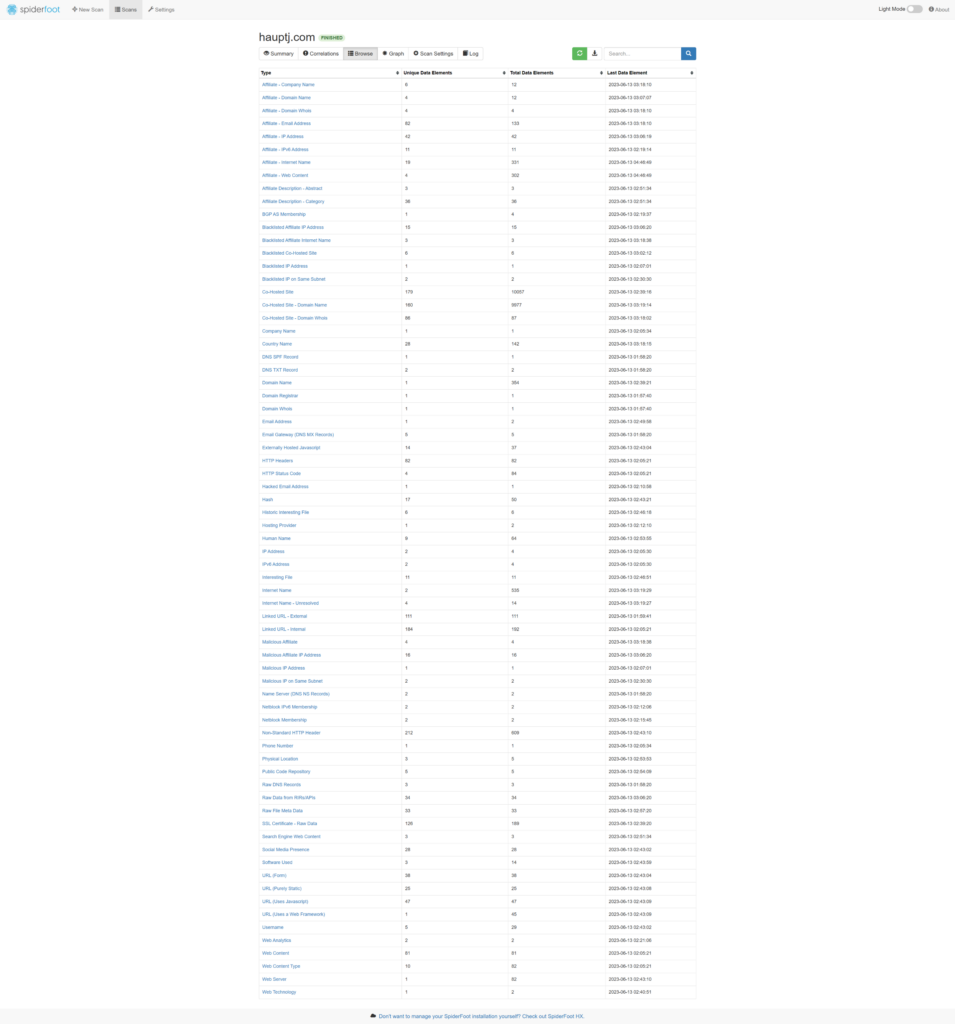
This appliance also includes an open-source intelligence (OSINT) automation tool known as SpiderFoot which utilizes external APIs as well as internal tools such as Nmap collect data on IP addresses, domain names, hostnames, network subnets, ASNs, E-mail addresses, phone numbers, usernames and crypto currency addresses.
I ran a lookup against my website, and it returned a large trove of information.
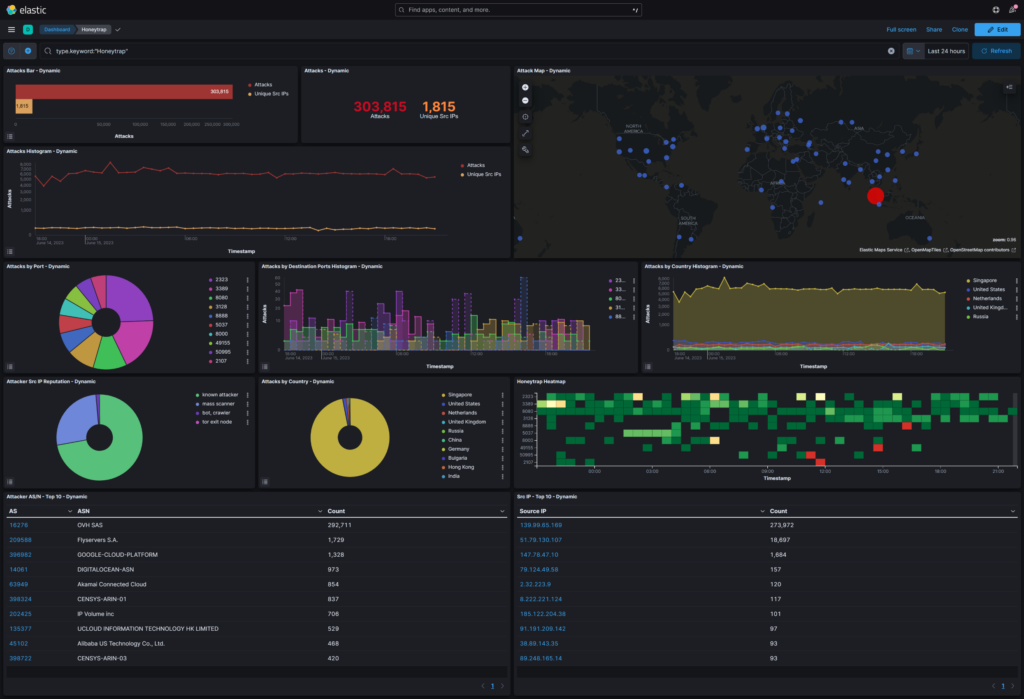
One anomaly I noticed was that there were numerous attacks against arbitrary non system ports originating from OVH’s datacenter in Singapore. These attacks were detected by HoneyTrap with the data being visualized in a Kibana dashboard.
T-Pot is resource intensive and uses over 8 GB of memory, so I deployed this instance on a basic, shared CPU, DigitalOcean virtual machine, in the NYC 1 region, with 16 GB of memory, 8 vCPUs, and 320 GB of SSD storage. Debian 11 x64 was used for the operating system as mentioned as the supported OS in the installation instructions. In order to simplify the installation process, I wrote a simple Ansible Playbook to automate the user configuration and the installation.
Leave a Reply